3- Operating Systems Operations
Most of the modern operating systems are interrupt driven. If there are no process to execute, no I/O devices to service, and no users to whom to respond, an operating system will sit quietly, waiting for some thin to happen. Events are almost created by an interrupt or a trap. The occurrence of an event is usually signed by an interrupt from either the hardware or the software. Hardware may trigger the interrupt by sending a signal to CPU, usually by way of the system bus. Software may trigger an interrupt by executing special operation called system call (also called a monitor call). When the CPU is interrupted is stopped what it is doing and immediately the execution to the fixed location. The fixed location usually contains the starting address where the service routine for the interrupt is located. The interrupt service routine executes, and on completion, the CPU resume the interrupted computing.
 |
| Interrupt timeline for a single process doing output |
The interrupt architecture must also save the address of the interrupted instruction. Much old design simply stored the interrupt address in a fixed location or in a location index by the device number. More recent architectures store the address on the system stack. If the interrupt routine needs to modify the processor state, for instance, by modifying register values, it must explicitly save the current state and then restore that state before returning. After the interrupt is serviced the return address is loaded into the program counter (program counter decide which would be the next instruction in the memory to execute), and the interrupt computation resumes, as though the interrupt had not occur.
An interrupt in the software can be generated either by an error (for example, division by zero or invalid memory access, unauthorized access of data) or by the specific request of the user to the operating system.. We need to sure that an error in a user program could cause problem only for the one program running. For example; if a process struck in an infinite loop, this loop could prevent the correct operation of many other processes. See the blow code for infinite loop in high level language.
while(true)
{
print("hasnainjamil.blogspot.com");
}
The while loop will run infinitely because the above code has no end condition. While loop will always true and generate an error to the compiler. Without protection against the sorts of errors, either the computer must execute only one process at a time or all outputs must be suspect.
It is important to distinguish between the execution of operating system code and user-defined code. We need two separate modes of operation:
An interrupt in the software can be generated either by an error (for example, division by zero or invalid memory access, unauthorized access of data) or by the specific request of the user to the operating system.. We need to sure that an error in a user program could cause problem only for the one program running. For example; if a process struck in an infinite loop, this loop could prevent the correct operation of many other processes. See the blow code for infinite loop in high level language.
while(true)
{
print("hasnainjamil.blogspot.com");
}
The while loop will run infinitely because the above code has no end condition. While loop will always true and generate an error to the compiler. Without protection against the sorts of errors, either the computer must execute only one process at a time or all outputs must be suspect.
3.1- Dual-Mode and Multimode Operation
- User Mode
- Kernel Mode (also called supervisor mode)
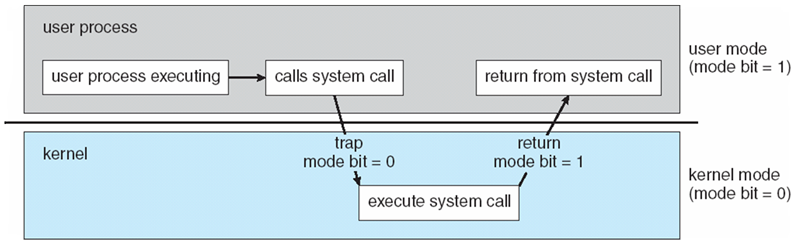 |
| Transaction from user to kernel mode |
At system boot time, the hardware starts in kernel mode. The operating system is then loaded and starts user application in user mode. The dual mode of operating system provides us with the means for protecting the operating system from errant users and errant users from another. Although most systems only distinguished between user and kernel mode. Multiple modes could be used to provide a finer-grained security policy. For example; if one user goes the kernel mode during execution to get their services. Perhaps another user same group may change the state of the mode. This risk is prevented by using multiple modes.
Sign up here with your email
ConversionConversion EmoticonEmoticon